Quite often when people say they have been “hacked” it turns out they haven’t been hacked. They’ve often fallen victim to something called “phishing”. That’s the term used when someone creates a fake website that looks like a real website to trick you.
You might often get emails that look like they are from your bank and then link you off to a website that looks like it’s from your bank – and they ask for all your login details – tricking you into handing over important information to the scammers.
Don’t feel too bad if you have fallen victim to this recently, or in the past. The web pages that people create for phishing are looking ever more real and professional. I discovered one recently that even went as far as getting a security certificate to show a little padlock icon to make you think you’re safe.
The Exodus Phishing Scam
I recently highlighted a phishing site pretending to be Exodus, but even after a manual independent review, the reviewers said there is “No threat found”. That’s because it’s a very convincing fake.
An email landed in my inbox claiming that 94,000 of Exodus customers have been hacked and need to update their 12 word seed phrase and pin number. Yet, I know that giving away your 12 word seed phrase and pin number is like giving a car thief the keys to your car.
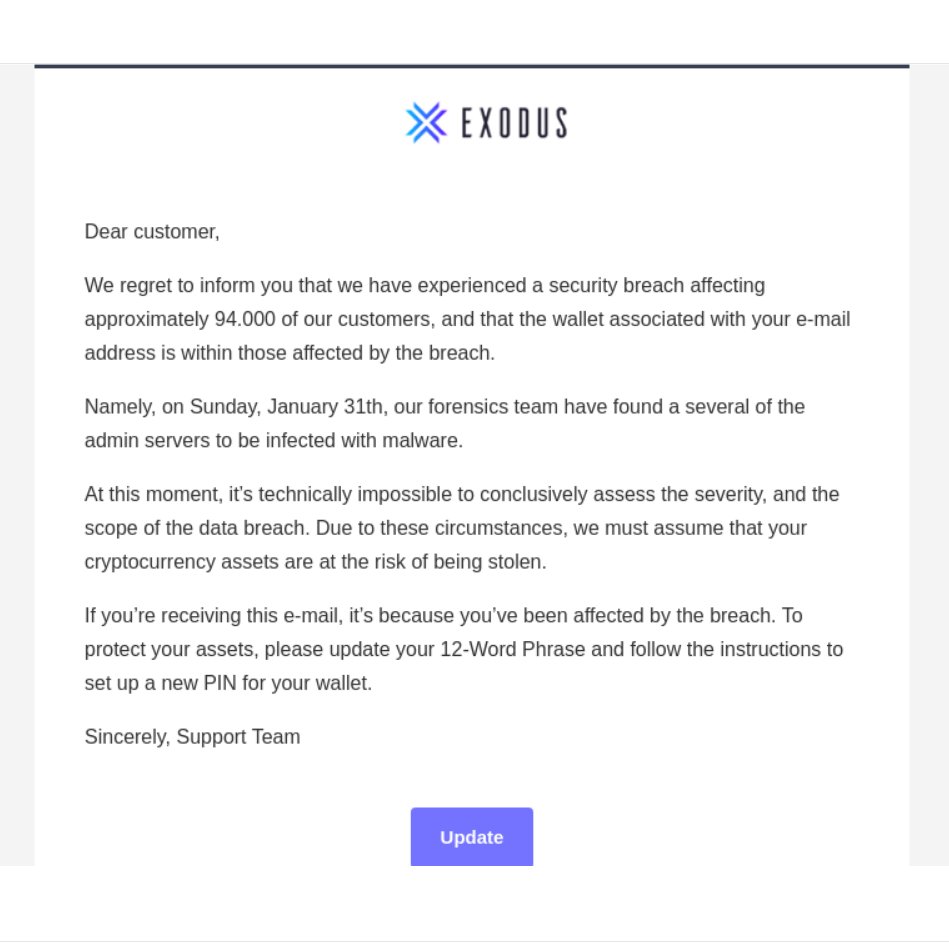
If you receive an email like this and you aren’t sure whether it’s real – do not click any of the links or buttons in the email. Close the email, open your web browser, and go directly to the Exodus website. This is a simple way to avoid getting phished from email; when the email is asking you to update or give some personal or security information never click any links in your email.
Clicking the link in the email might save you the 10 seconds it takes to open a web browser and type in the website name yourself – but spending the 10 seconds to do it manually will save you from getting phished.
But since I know what I’m doing…
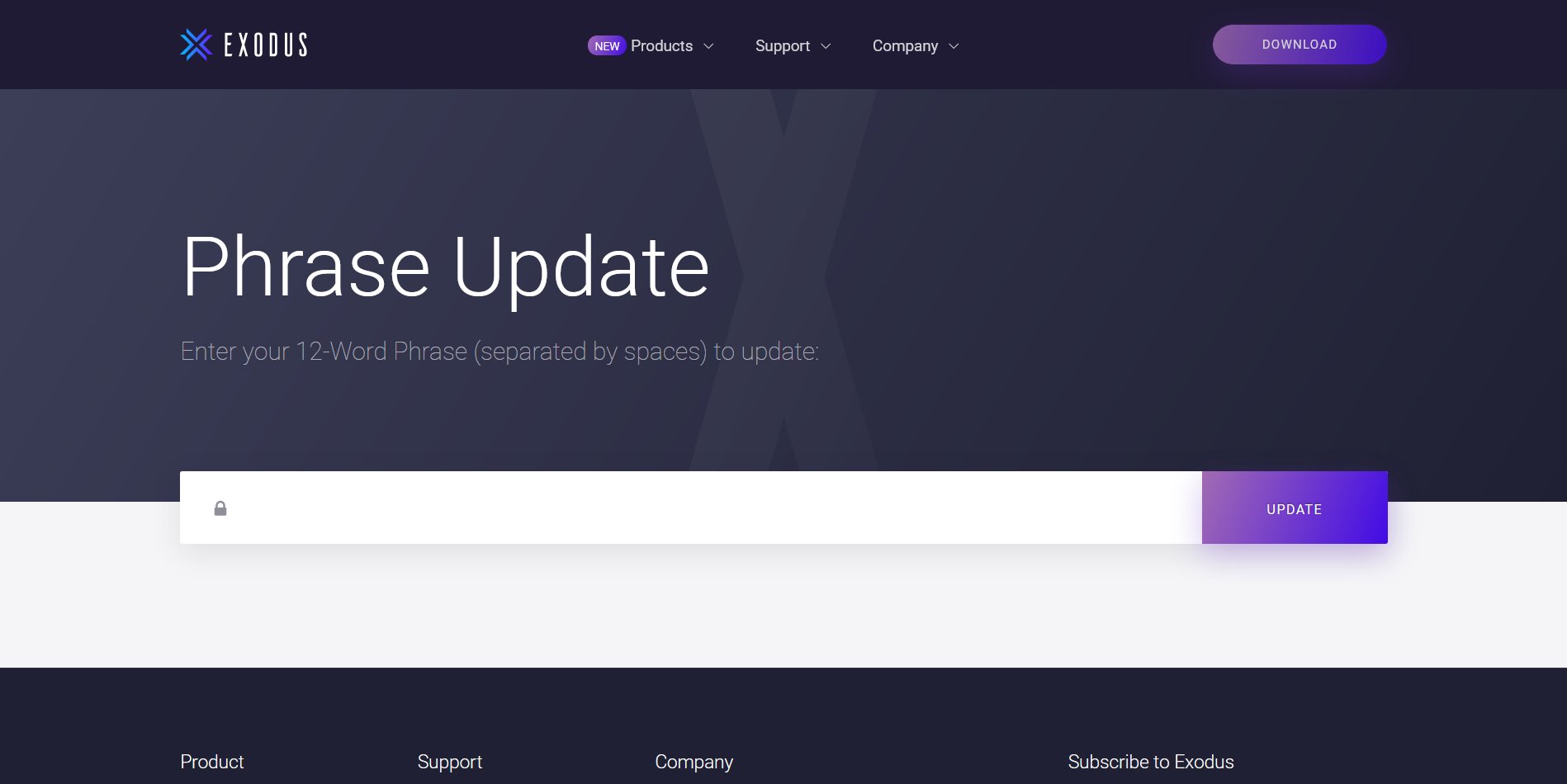
I clicked the “Update” button. It takes you to a fake website which had my email address added to the end. This helps make it look legitimate, but also for the scammers to know I’ve been blind enough to fall for the scam.
Everything looks like the official Exodus website. If I do a web search for ‘Exodus wallet support‘ I will find the official support website. At the time, this was http://support.exodus.io and the website I was taken to by the email was not exodus.io.
Here is a comparison of the fake site, versus the real one.
Looks pretty real, huh?
There are sections of the Exodus Support website which say that they would never ask for your 12 word seed phrase. No website or customer support should ever need to know your seed phrase and so alarm bells should ring at this point.
And whilst the fake site looked real, the scammers will rarely copy the whole website. This means that clicking the navigation doesn’t go anywhere. The Products, Support, Community, and Download links all keep you on the same page, asking for the seed phrase.
But, this looked like an official email. And the website looks quite real. And if I look in my web browser, there is a little padlock assuring me the website is safe!
Wrong.
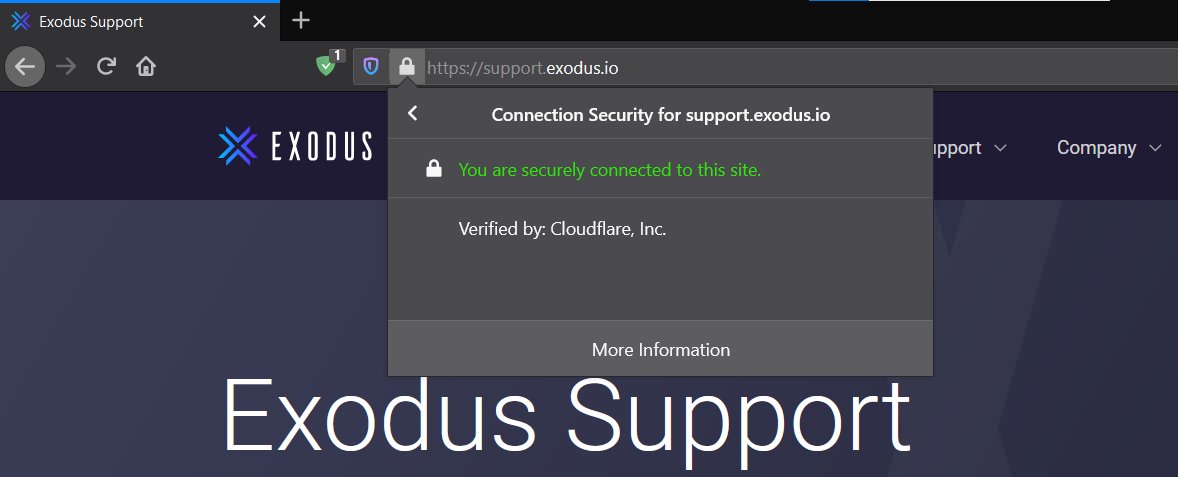
We’ve been told to trust the padlock. If you see a padlock in your browser, the connection is secure – everything is safe, right? But this just means the you have a safe connection between your computer and the website you are visiting. The padlock doesn’t tell you if the website is real or fake. If that website is a scam website, the padlock confirms you are safely connected to the scam website. Nothing more.
On closer inspection — the official Exodus team use Cloudflare to verify the connection to their website. The fake site uses a different provider; Let’s Encrypt. There is no good reason why one company would use two different companies to issue their security certificate.
This isn’t something I would expect most people to pick up on. On seeing the padlock, people presume the site must be legit. But in this case, it’s not.
These are the biggest tell-tale signs:
- The email is asking you to update or provide personal or security information AND provides a quick link to click to update your details.
- The website address is not the same as the official website — if you are unsure, use a search engine to get to the official website before signing in or giving away information.
- Often, none of the other links on the website work. This is not a fool-proof way of detecting a scam, but you can try clicking around the site before you start entering information to see if the website is real.
- Don’t enter information on a website without the padlock icon. But also know that the padlock icon doesn’t tell you whether the website is real or fake.
How to report phishing
If you receive an email or find a website you think could be trying to trick you out of some information, you could simply ignore it or delete it. However, there are people out there who aren’t as savvy or aware as you – and with just a few clicks, you can help protect them from falling for the scam.
A lot of the big tech companies try to stop you getting scammed. If they know a scam site exists, their apps will jump in and tries to protect you. It sometimes looks like this:
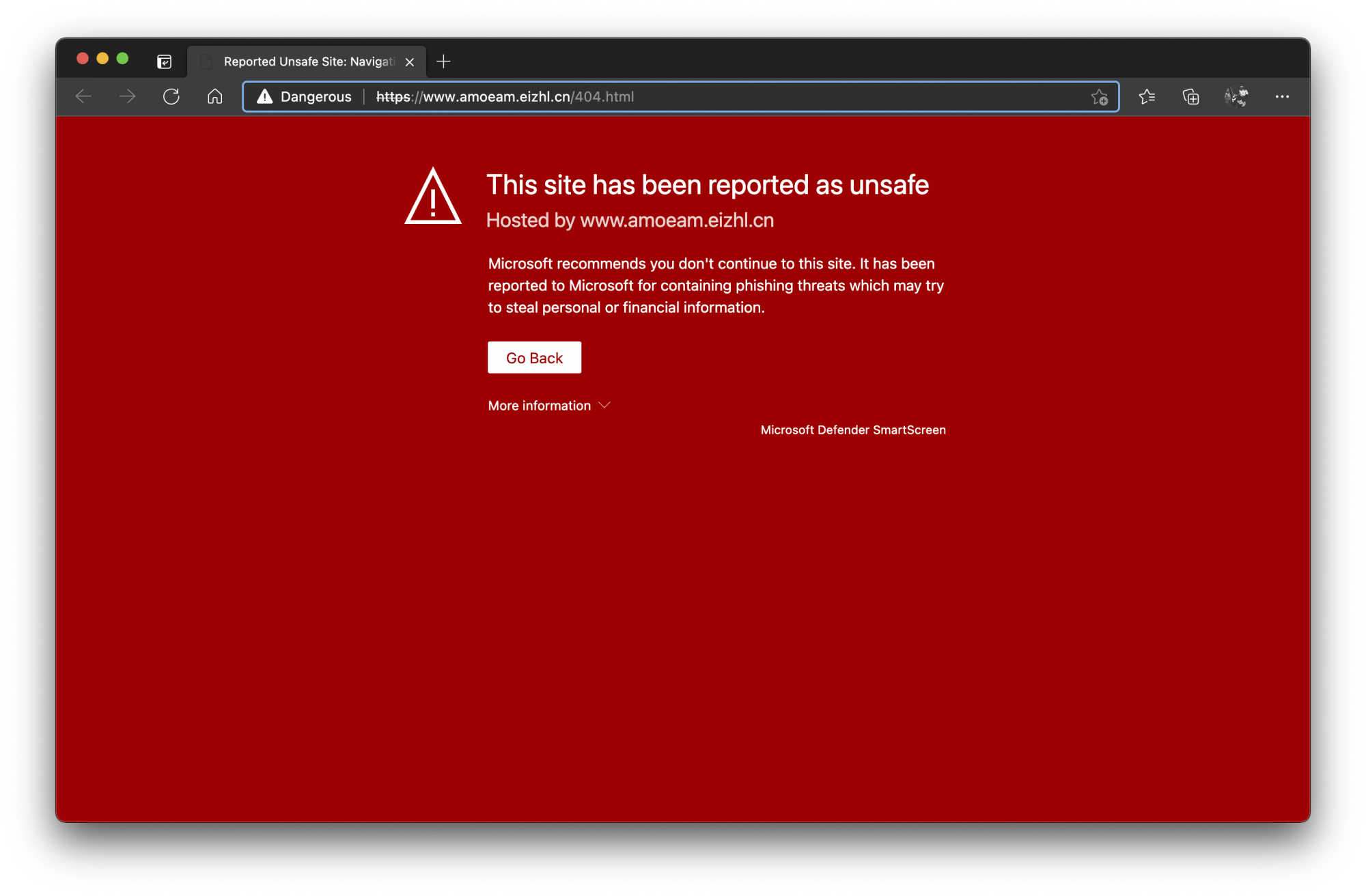
But to know these sites exist, they need people like you to report them. And you can do that in a few different ways; by email address, or visiting a website.
Reporting phishing by email
This is a very straight forward approach. You receive a phishing email and before you delete it, choose the “Forward” option in your email app and send it to one or all of these email addresses:
phish@phishtank.com, scam@netcraft.com, phish@office365.microsoft.com, report@phishing.gov.uk
This will send the fake email and any websites to companies like Phishtank, Netcraft, and Microsoft who decide whether they think it’s a phish or not. If they do, they’ll block it for everyone.
Interestingly, the last email address sends it to the UK Government who as of 31st March 2021, received more than 5,500,000 reports and work with hosting companies to remove links to malicious websites.
Report phishing manually
Google! That’s the big one. There are so many Google Chrome users that you should probably report any phishing to Google. Unfortunately, they don’t have an email address to forward your junk to. You have to use the Google Safe Browsing Report a Phish form.
This means you’ll have to manually copy and paste links across into the form. So tedious. I’d expect something more from Google, but it is what it is.
Russia’s answer to Google – also allows you to manually submit sites to Yandex. This means people using Yandex browser for desktop and mobile, Yandex mail, Yandex DNS and other Yandex services I don’t really know about will benefit from your reports.
You can report manually to both Phishtank and Netcraft too, but they have the email address for quick-submission.
Stay safe
So, that’s pretty much it. Be aware of what you are clicking on and what information you are about to leak.
If you find a phish, help others catch it first by reporting to the email addresses or websites mentioned above.
Good luck out there on the wild west web.
If you ever want to geek out and chat with me about internet privacy and security – drop me a message via Matrix to @matt:gossip.land or via Mastodon to @matt@oslo.town


Leave a Reply